This is gonna be a thread related to the mobile proxies, questions how it works, what is based on and other basic moments to get a better understanding of what is mobile proxy actually is. Let’s go
The formula of mobile proxies is quite simple:
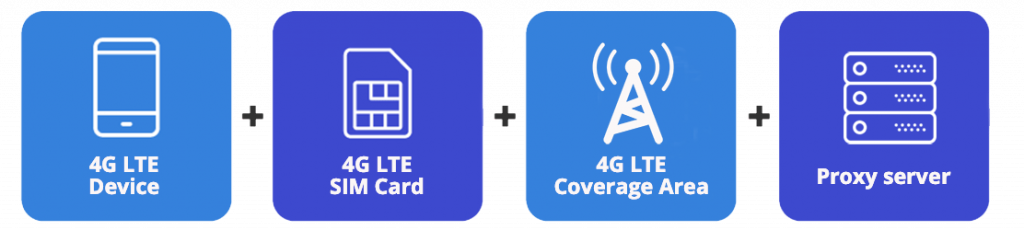
The mobile proxy is based on IP addresses of the mobile (cellular) internet provider – ISP. It redirects traffic using proxy server via mobile hardware – mobile phone or LTE dongle which is connected to the cellular network. Proxy server its a setup of software and hardware which is some “bridge” between the user and ISP what allows in its order to use the mobile connection wherever it’s needed. Such proxies provide an extra layer of anonymity and trust, that’s why they may be useful in certain business-related scenarios, such as management, parsing (web scraping) or even spam.
What is a mobile proxy?
If to say simply – mobile IP address is just an address which is given to the LTE device by the mobile cellular provider when it gets connected to the network. Without taking into account, to create a mobile proxy is LTE hardware and LTE sim card, the main difference between mobile proxy and the common data center proxy is an IP address its based on and the trust level of mobile IPs. An integral part of mobile proxies is access to the all IPs in wireless carrier’s pool, which includes thousands of addresses that will be used dynamically. But first things first – firstly let’s take a look on at LTE network architecture

The current architecture is quite simple, and a lot of parts of the LTE connection chain were removed to make it clear and focus on the main aspects. Thus this scheme demonstrates, that every LTE device (mobile phone or dongle for example) connects to the cell tower, gets an IP address and then go to the public internet (the web). At this step, all must be clear.
What is 4G LTE?
The LTE stand (Long-term Evolution) networks were designed because the speed and the bandwidth of the previous generation of 3G stand simply was not enough to meet the needs of the constantly growing volume of data transfer it should be sent. The ITU-R set standards for 4G connectivity in March 2008, requiring all services described as 4G to adhere to a set of speed and connection standards. For mobile use, including smartphones and tablets, connection speeds need to have a peak of at least 100 megabits per second, and for more stationary uses such as mobile hot spots, at least 1 gigabit per second.
When these standards were announced, these speeds were unheard of in the practical world, because they were intended as a target for technology developers, a point in the future that marked a significant jump over the current technology (meaning 3G stand). Over time, the systems that power these networks have caught up, not just in the sense that new broadcasting methods have found their way into products, but the previously established 3G networks have been improved to the point that they can be classified as 4G.

LTE stands for Long-term Evolution and isn’t as much a technology as it is the path followed to achieve 4G speeds. For a long time, when your phone displayed the “4G” symbol in the upper right corner, it didn’t really mean it. When the ITU-R set the minimum speeds for 4G, they were a bit unreachable, despite the amount of money tech manufacturers put into achieving them. In response, the regulating body decided that LTE, the name given to the technology used in pursuit of those standards, could be labeled as 4G if it provided a substantial improvement over the 3G technology.
Immediately networks began advertising their connections as 4G LTE, a marketing technique that allowed them to claim next-gen connectivity without having to reach the actual required number first. It’s not entirely trickery though, despite inconsistent speeds depending on location and network, the difference between 3G and 4G is immediately noticeable.
To make matters more confusing, you’ll also likely come across LTE-A at some point. This stands for Long-term Evolution Advanced, and it takes us a step closer to proper 4G. It offers faster speeds and greater stability than normal LTE. It’s also backward compatible and works by aggregating channels, so instead of connecting to the strongest signal in your vicinity, you can download data from multiple sources at the same time.
But, the reality is: now 11 years later since the LTE stand was announced the volume of transfer data were highly increased as well as a number of LTE devices in general around the world. According to the Hootsuite report by April 2019 here are the numbers which demonstrate the number of mobile users and mobile connections.


Due to the growth for the number of mobile connections and mobile devices around the world – the speed of LTE networks and its bandwidth dramatically drops especially during business hours. Thus the speed instead of promised 100 Mbps my vary around 30-50 Mbps and even drop up to 20 Mpbs in densely populated areas and business centers. For the marketers and managers is not that big a deal, because even 20 Mbps is more than enough and these speeds allow uploading content or perform some actions with no general issues at all. The more important is a ping or response time.
Ping
Ping is a term that relates to a test to find out how fast a data signal can travel from one place (your computer) to another place (a website, usually).

Ping started out as a program that allows you to send out a test signal to another computer to see if it exists and how fast it responds. Ping sends a “packet” of electronic data to a specific IP address and “waits” for an electronic signal/tone that’s known as a “pong.” (“Waiting” for the pong is an inaccurate term: It takes a brief moment to get the response back.)
Ping is not an acronym or short for anything. It is sometimes thought of as the backronym packet Internet groper. The word “ping” comes from the sound sonar generates when it detects objects underwater.
In computer gaming, a ping, also known as a high ping or low ping, is a measurement of how fast of a connection to the game server the player has. For example, a player with a low 50 ms ping is going to have a better gaming experience than a player with a 250 ms ping.
The same way it’s working with the proxies, the ping identifies how fast the data from software would be sent to the global internet, processed at the destination and returned back. The lower ping the better.
What is a Good Ping Response Time?
< 30 ms – excellent ping; almost unnoticeable
30 to 50 ms – average ping; still ok
50 to 100 ms – somewhat slow ping time; not too noticeable for web browsing but may affect gaming
100 ms to 500 ms – slow ping; minimal effect on web browsing, but will create noticeable lag in online gaming
> 500 ms – pings of a half-second or more will add a noticeable delay to all requests; typically happens when the source and destination are in different parts of the world
We should know the ping and the response time is a bit different terms, while we are talking about proxies in general and as well the wired (data center proxies) and the wireless (mobile proxies) connections. Ping is the speed with the proxy server where the proxies are set sends the data signal to the destination, while the response time is a time which is needed specific software to connect to the proxy server and send a data signal to the final destination. Obviously, the response time would be higher rather than ping.
Also, it should be noted hows good would not be the wireless networks – the wired still are better, and according to the numbers of mobile users around the world, the ping of wireless LTE networks so far behind to wired connections. It’s not critical, but still. That’s why the average software response time with the usage of mobile proxies should be around the next numbers:
<1500 ms – pretty good response time
2000 – 5000 ms – quite allowed response time, lags almost invisible
5000 – 10 000 ms – rare lags, still nothing serious in general
10 000 – 15 000 ms – quite problematic to use but still possible with proper patience
> 15 000 – almost impossible to use
The response time directly depends on the proxy server location and the software location. The more the distance between them – the more time is needed to complete the request. That’s why when going to order the mobile proxy server – much better would be if the mobile proxy server and the server with installed software (software which will use the proxies) are located in the same continent at least.
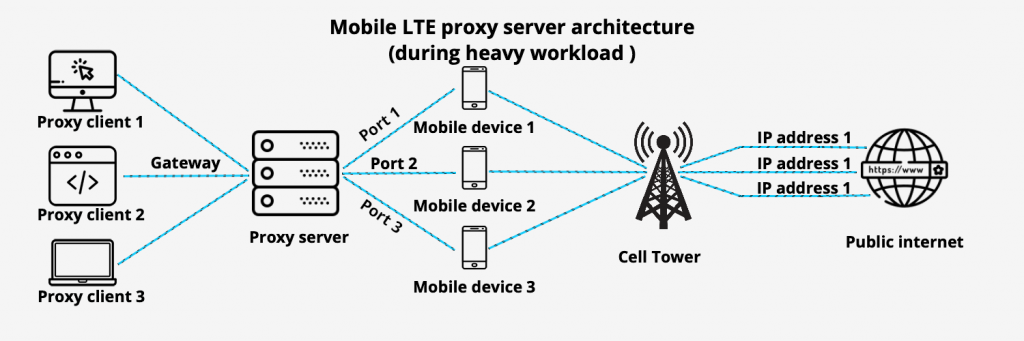
And finally considering on the information above, such like: number of mobile devices, number of mobile connections, bandwidth, and cell tower workload, during the business hours, the LTE network architecture mat look this way:

This scheme might shock someone, but cell carriers have only a limited number of IPv4 addresses and dedicate user’s IPs from own pool. So a few millions of users share just a couple of hundreds of IPs distributed between devices using NAT.
For example, the Vodafone UK by May 2019 has 17,2 million active mobile users.

At their disposal, according to the open data from the web – the Vodafone has two subnetworks 212.183.X.X 0/20 and 194.62.X.X /20 of which provides IPs to its subscribers (mobile users). Each subnetwork has around 65 000 IPs inside. The equal number is 65,536, so both subnetworks have in total 131,000 of IP addresses which are shared between all the Vodafone users.
In average, the number of subnetworks for every single cellular provider may varify from 1 to 3. It’s a worldwide practice and rarely this number exceed the rate of 4 for the super big providers. Anyway, if to get back to the Vodafone, it would be quite simple to calculate that every IP address is shared with 131 users in general, or other words every 131 users are using the same IP address.
At this step it should be absolutely clear – any kind of mobile proxy could not be private, never used or virgin. We will get back to this step a bit later in this thread and explain deeper why.
Now, this is how the Mobile LTE proxy server architecture looks like:

Now when the basic principles of performance of mobiles proxies became clear, we can take closer to such aspects as a rotating mobile proxy.
To be or not to be. To rotate or not rotate?
Around the web exist two views about rotating proxies: the first prefer static proxy only and absolutely sure its the best solution for the management, because additional and/or frequent changes of the IP may trigger additional issues, while the second prefers to use rotating proxies exactly, because it allows getting fresh IP with the specific interval or by request. And the good question arises – “Who is right and what kind of proxy to choose ?”
To provide an answer lets take a look at what is a static proxy in general. The common static proxy to a large extent is a static IP address which never changes under no circumstances, while the rotating proxy is an opposite to static proxy, where the rotating possibility depends on the proxy server settings or/and user request.
To change outgoing proxy IP – the LTE device proxy is based on should be reconnected, but except that cellular provider may switches the device (connection) to another cell tower, due to the tower workload or the simple to the nearest cell tower according to the geolocation. The first case is called a manual or software proxy rotating, and the second is called as basic rotating. In general, the mobile cellular provider rotates the IP (switches the connection) 2-3 times per day. That’s why the “static mobile proxy” simply doesn’t exist.
The term “rotating proxies” appeared with an appearance of “general rotating” datacenter proxies. Such type of proxies represented itself, proxies where outgoing IP changes with the specific interval, but in addition besides the IP changes the geolocation as well. With every new request the user gets Ip from a different country, for example, USA – Italy – France – Portugal and so on. Obviously, those type of proxies could be used for gray or black hat methods and it absolutely has nothing to do with the management of advert companies in facebook or Instagram accounts which uses mobile rotating proxies. The term “rotating proxy” is a trigger in some way, and mistakenly or unconsciously people sometimes link the terms “rotating proxies” and “mobile rotating proxies”. That is incorrect, because while the mobile proxy (IP) rotates – the user or attached account gets a fresh IP address from the same location, same ISP and sometimes even from the same cell tower. It’s not an issue and that’s why it becomes possible to use such type of proxies for the white hat actions such as management.
What is the difference between rotating and “static” mobile proxies?
Anyway, the difference must exist, because otherwise there would be no reason to create rotating mobile proxies. The main task of mobile rotating proxies is to provide the user the opportunity to change the outgoing IP when it’s needed. Originally the mobile proxies were designed for usage with Instagram in general, when appeared the general term of “action blocked” and the solution for that was to switch from data center proxies to more quality due to the trust level – mobile proxies. Then, as always Instagram updated they algo, and there appeared then next type of “action blocked” where the reason was too fast or too many actions (request sent) from the specific IP. Approximately at the same time, Jarvee software team released a new feature, which still exists and is called as “suspend tool when the action is blocked”. When the account gets a temp action block – software stops the tool, the account rests for the specific period set by the user and in a complex with rotating mobile proxy gets the new fresh IP and continue the actions – that’s exactly the main idea of mobile rotating proxies.
With the recent Instagram update on June 1, 2019, when the number of allowed “follow” actions were reduced to the around 6000 per month or 200 daily – borders between “static” and rotating mobile proxies has decreased. Since the allowed number of the actions were reduced, then and a workload on the IP was reduced too, that’s why if the account which is attached to the “static” mobile proxy gets an action block – it would be disappeared almost as fast as if it would be attached to the rotating mobile proxy.
That’s why answering the question: “Which type of proxy is better – “static” mobile or rotating mobile – the answer will be depending on the future type of usage: “For white hat management both of them would be good. For the grey hat methods such as “mother-child” or bulk account creation – rotating would be better because it allows changing IP”
The next exciting questions sound as: “Is it possible to blacklist mobile proxy ?”
Is it possible to blacklist mobile proxy?
But you have to ask yourself, what is a flagged, blacklisted or low-quality mobile proxy? How to identify it and based on what kind of factors such a decision could be made on.
Usually, people attend to say the proxy is flagged or low quality when they get some issues while using the specific proxy. It could be endless phone or email verification loops, a lot of blocked actions, impossibility to publish a picture or to get banned accounts and so on. And when something like that has happened – it’s adopted to say the proxy is flagged. On one hand, it’s absolutely clear, got the issues the proxy is flagged. Right?
But on another hand, every single social network has its own closed database of blacklisted Ip addresses, which never would get into the public. Otherwise, it would be super easy to detect for every spammer what pool IP is clean and which one is not. Also, know the politics of the social networks, when sometimes it becomes impossible to reach its support (say hello to Instagram) they would never share its private information. And also there is such thing as account’s trust level which identifies what is allowed to the account and what is not even with the best proxy ever.
Never the less there are exist some services which may help indirectly to identify the general quality and purity for the proxy:
Whoe.net 6 Its a super useful website which allows instantly identify outgoing/external or real in other words IP address and security leaking if its existence. Take a look – its very important to go to whoer.net 12 under the proxy exactly. All you have to do is set up the proxy in your desktop browser, for example, FireFox or to use EB (embed software browser). In addition, depending on what is used – desktop or EB – you might get different results, because, at Jarvee for example – security leaking sources like web rtc, java or flash is disabled by default, while in your desktop browser it might be enabled as well. Anyway if something is wrong – the web site will notify you and what is more important it will let you know how to fix the issues.

Once you open the whoer.net 12 – the first you have to look at is
- My IP – External/outgoing proxy IP address
- ISP – ISP (internet provider)
- DNS – location of proxy and DNS location should match. Not a big deal if it’s not, because quite often as additional DNS is used google DNS. It’s a worldwide practice, so do not worry if it does not
- Anonymity bar. If something is wrong with the proxy or its too much known about you/your location due to security leaking of web RTC, java, flash, different time zones, language difference (you location and proxy location) and so on – the web site will let you know.
ip2location is another good and useful website which helps to get more information about IP address (proxy) and its affiliation. Exactly at this step, we will be able to identify is the proxy mobile or data center IP based.
So, here we go:

All you have do is to paste the IP address you want to check or click the “lookup” button to verify your current IP. A few seconds later there will be a result like this one:

The main data is:
- ISP – internet provider
- Mobile carrier. If the proxy is a real mobile – this option would be available, like on a screen above – Vodafone.
- Usage type. Additional confirmation of proxy affiliation.
- Proxy type, ASN, Proxy Last Seen. By default, it has nothing do with the proxy itself and identification depends in general on browser settings like on example above with whoer.net 12
By the web site description, it was designed to identify the purity of the proxy. The web site verifies the availability of proxy (IP address) in dirty or blacklisted spam bases. For the sake of justice, we have to admit getipintel.net 5 doesn’t have access to private bases of Instagram or Facebook for example. It checks only public open Ip addresses bases. Anyway, this service might be used as an additional IP address verification tool. All you have to do is to paste IP address you want to verify and press the “lookup” button.
Of course, when it’s about the data center proxy to identify flagged proxy is quite easy. If the proxy is shared or cheap for example like IPV6 /48 proxy – yes it could be easily banned. But the mobile proxy (IP) is shared by default with the other real mobile cellular users, so in this case, this rule simply doesn’t work.
Let’s imagine, after all – mobile proxy (IP) could be blacklisted for some reason and due to some kind of actions. As you already know “static” mobile proxy (IP) doesn’t exist, thus soon or later the whole pool of the IP addresses would be blacklisted. What’s next – the real users of ISP who uses the same IPs would be affected too, they will not be able to use the specific web sites or social networks, as a result, the cellular provider will lose the clients and, guess who will lose the customers ultimately? The social network which started blocking IP addresses of the real users, which would lead to its financial ruin. I hope there is no reason to explain money is the blood of business. Social network it’s a business, its blood is the users. That’s why mobile proxy would never be flagged! With kind regard to the owner of Facebook and Instagram, seems he loves money too much  – its one more reason why they will not do that.
– its one more reason why they will not do that.
If the mobile proxy so amazing and cant be flagged, why I still have issues?
It’s another good and frequent question. As it was told above – mobile proxy (IP) couldn’t be blacklisted, but actually, it’s not needed. The times when it was possible to switch to the mobile proxy and avoid almost all the issues are gone. Instagram developers do no sleep, they know what is going on around here, how it works and which way the wind blows. Since Instagram is a superb social network, the main goal of its owners is to keep it clean as much as possible, that’s why they have constantly updated the algorithms which track actions of million accounts and based on type and number of the actions identify who is who. What is the account of the real user and what is the account which uses automation software, which account must be banned and which may run calm
A bit of offtopic: Does someone of you believe mobile devices or installed apps may watch you or track your conversation? Have you ever noticed you chat with your friend in the messenger or talking via mobile phone about some specific subject and then booms a few days later you see related advert it the web? Yes, I know its called a targeting. But what if you never searched for this specific information in google and now see related ads? A bit bizarre. Of course would be much easy to belive big brother is watching you, probably its true and even Shazam app developers confirmed they app is always active and listening to you providing your better and faster-using experience, but they do not record you (maybe). Actually, all is clear: if at least one of the participant of the conversation will google something, then it request would be tracked by the search engines, social networks he signed up and so on. Then if you are friends in some social network or emailing each other and provide access to your phone book or browsing history, once the target engine finds the crossing in the interest, location, age, and other data between your and your friend – you will see the advert.
In this case, the question is not do they watch for or not. The question is what is easier? Right targeting would be easier than to watch for everyone and analyze its conversations.
About the same works of Instagram algorithms. And obviously, they have some level for identifications, starting from the account created method, history of actions and ending with the sending request in a background. Actually, it’s not a joke, recently we noticed Instagram checking availability and access to the phone book on a mobile phone – have no idea why they need it, for some kind of future targeting or for the identification whether a mobile phone is used or automated software.
Conclusion:
To sum up, I would remind again, private, static, virgin never used mobile proxy its a myth. Such type of proxies doesn’t exist. The term “private” proxy means the specific proxy is sold in one hand only and used by proxy sellers. The mobile proxy couldn’t be blacklisted and it’s almost impossible to identify whether the proxy is flagged in specific web resource or not. Only some resource may show the purity of the proxy and check its affiliation. Answering the main question: “What is mobile proxy – marketing or sacred grail?” the answer would be: “Its no marketing either sacred grail. Mobile proxy is just a must-have part of the right and correct working setup, but it’s not enough. The most important factor always been and always will be the actions. Type, number and randomization of actions “
P.s. If someone of you guys, wants to add some info, edit or correct - feel free to do that.
Thanks for reading and good luck 
Source: https://mpsocial.com/t/info-post-mobile-proxies-what-is-it-marketing-or-sacred-grail/83117